- Docker Docker Daemon Json Config Example
- Docker Docker Daemon Json Config File
- Docker Docker Daemon Json Config Tool
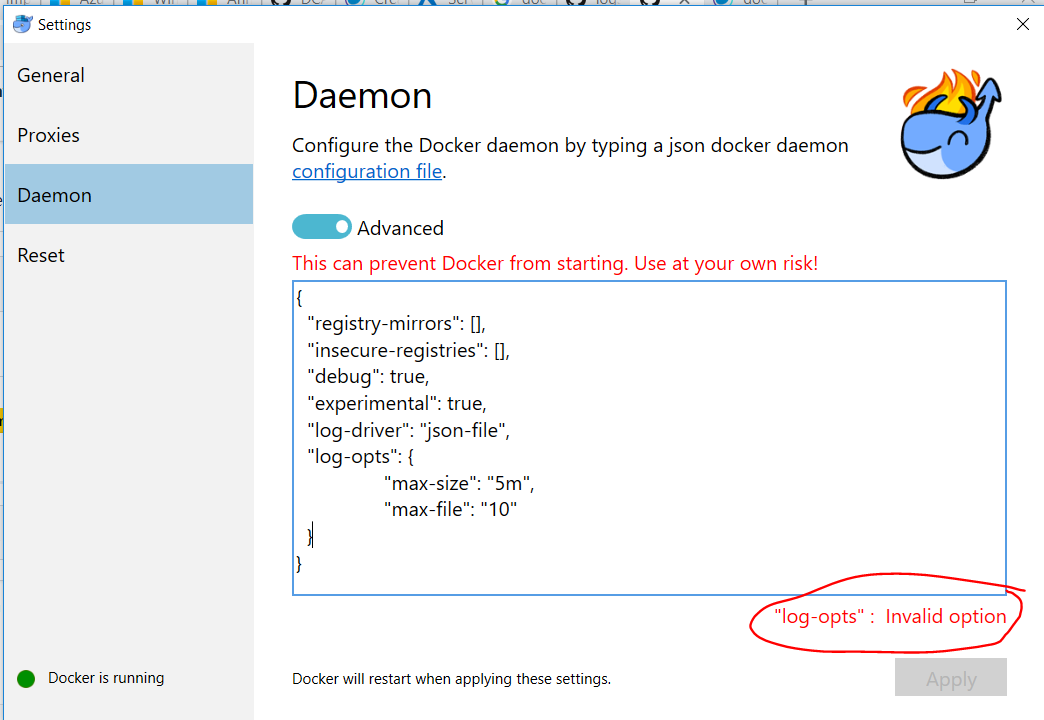
Daemon.json is the file name which is being used to Configure Docker daemon. There are two ways to configure the Docker daemon: Use a JSON configuration file. This is the preferred option, since it keeps all configurations in a single place. Mar 18, 2019 The -config-file option allows you to set any configuration option for the daemon in a JSON format. This file uses the same flag names as keys, except for flags that allow several entries, where.
Example of daemon.json or docker.conf – Complete Options. Rajesh Kumar March 31, 2020 comments off. Usage: dockerd COMMAND. A self-sufficient runtime for containers. Options: -add-runtime runtime Register an additional OCI compatible runtime (default ) -allow-nondistributable-artifacts list Push nondistributable artifacts to specified.

So in P3 of the Harden Docker with CIS series, I’ll continue with the hardening process of the Docker installation which we setup in the P1. We’ll start with the module two of the benchmark (CIS Docker Benchmark v1.2.0) i.e. Docker daemon configuration. There are seventeen items in total out of which one is “Not scored”, thus. For daemon.json case, there isn't a command to list all the effective configuration for docker daemon, and I even don't know whether dockerd read the daemon.json I create, or which daemon.json it tried to read.
Step 2 in the Linux setup for the ServiceNow® headless browser for Automated Test Framework.

Role required: admin on your ServiceNow® instance and local administrator on the host machine.
Complete step 1: Generate certificates for headless browser setup for Linux
Procedure
- Configure Docker to use the certificates you generated in Step 1.
- Find or create the /etc/docker/daemon.json file.
- Add the following properties to the daemon.json file. Be sure to replace with the correct paths to your certificates: To learn more, see https://docs.docker.com/config/daemon/#configure-the-docker-daemon.
- Configure Docker to expose the remote API on a port (Port 2376 is recommended).You can configure Docker to accept remote connections with the docker.service systemd unit file for Linux distributions using systemd, such as recent versions of RedHat, CentOS, Ubuntu and SLES, or with the daemon.json file, which is recommended for Linux distributions that do not use systemd.
If using systemd (systemctl):
- Use the command
sudo systemctl edit docker.serviceto open an override file for docker.service in a text editor. - Add or modify the following lines, substituting your own values.
- Save the file.
- Reload the systemctl configuration.
sudo systemctl daemon-reload - Restart Docker.
sudo systemctl restart docker.service
If not using system:- Set the host’s array in the /etc/docker/daemon.json to connect to the UNIX socket and an IP address, as follows:
{ 'hosts': ['tcp://0.0.0.0:2376']} - Restart Docker.
- To enable Docker access via a command line, add the certificate authority public key and client keypair to the .docker directory. Copy the CA public key, the client public key (be sure to name it key.pem), and private certificate (be sure to name it cert.pem).
- Copy certificates to the docker home directory.
mkdir -pv ~/.dockercp ca.pem ~/.dockercp client-key.pem ~/.docker/key.pemcp client-cert.pem ~/.docker/cert.pem
- Set DOCKER_HOST and DOCKER_TLS_VERIFY environment variables for your user:
- Use the command
Docker Docker Daemon Json Config Example
- unable to configure the Docker daemon with file /etc/docker/daemon.json: the following directives are specified both as a flag and in the configuration file: hosts: (from flag: [fd://], from file: [unix:///var/run/docker.sock tcp://172.0.0.42:2375])
- systemctl list-units
- Erste Zeile: '# /lib/systemd/system/docker.service'
- Problem: ExecStart=/usr/bin/dockerd -H fd://
- Entferne -H fd:// (auskommentieren reicht nicht)
- systemctl daemon-reload
- 'hosts': ['unix:///var/run/docker.sock', 'tcp://0.0.0.0:2375'],
- docker -H localhost:2376 --tlsverify --tlscacert=ca.pem --tlscert=client-microtest-cert.pem --tlskey=client-microtest-key.pem ps